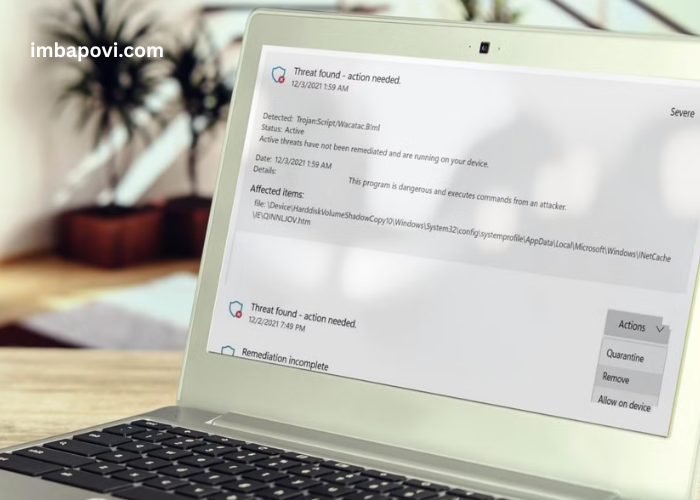
In today’s digital world, cyber threats are a constant concern, and one of the most sneaky and dangerous types of malware is the Trojan. Among these, Wacatac, also known as Trojan: Win32/Wacatac, has earned a reputation for its ability to silently infiltrate systems, cause severe damage, and steal sensitive data.
The most troubling aspect of this Trojan is its ability to operate in the background without detection. This article will delve into the dangers of Wacatac and provide helpful advice on how to detect and remove it from your system.
The rise of cybersecurity threats has forced both individuals and organizations to become more vigilant about protecting their computers and networks. While there are numerous types of malware, Trojan: Win32/Wacatac stands out due to its stealthy behavior and severe impact on the systems it infects.
It is a Trojan virus, which means it pretends to be a legitimate program or file in order to trick users into downloading and installing it. Once inside, it can steal valuable information, corrupt files, and even allow cybercriminals to take control of the infected device.
As we explore the hidden dangers of this Trojan, it is essential to understand how it works, how to detect it, and most importantly, how to protect yourself and your system from it.
Key Points:
- Wacatac is a Trojan-type infection that infiltrates computers undetected.
- It can steal sensitive data and compromise system performance.
- Proper security measures and regular scans are essential for prevention.
What Is Trojan: Win32/Wacatac?
Trojan: Win32/Wacatac is a type of Trojan horse malware that targets Windows systems. Trojans, in general, are malicious programs that disguise themselves as legitimate software to trick users into installing them. Once installed, Wacatac can cause significant damage to your computer and can sometimes go undetected for long periods of time. It typically spreads through malicious attachments, unsafe downloads, or phishing emails that trick users into running the infected files.
How Does Trojan: Win32/Wacatac Infect Systems?
The most common way Wacatac spreads is via phishing attacks or malicious email attachments. Once the user opens a malicious email or downloads an infected file from an untrusted source, the Trojan enters the system. It often runs silently in the background without any noticeable signs of infection. This makes it particularly dangerous, as users may not realize that their system has been compromised until it’s too late.
Note: Trojan: Win32/Wacatac infections can also spread through pirated software or compromised websites. Always ensure you download software from reputable sources.
Trojan: Win32/Wacatac – Features and Capabilities
| Feature | Description |
| Stealth Mode | Runs undetected in the background without alerting the user. |
| Data Theft | Can steal sensitive personal information, including passwords. |
| System Corruption | May corrupt or delete files, affecting system performance. |
| Remote Control | Allows cybercriminals to take control of the infected system. |
| Spreads via Phishing | Often delivered through infected emails or malicious links. |
How Can You Detect Trojan: Win32/Wacatac?
Detecting Trojan: Win32/Wacatac is not always easy because it hides its activities very well. However, there are some signs that can indicate an infection. Here are some common symptoms that users should look out for:
- Slow System Performance: If your computer has become unusually slow, especially when opening programs or accessing files, this could be a sign that malware is using system resources.
- Unexpected Pop-ups and Errors: A sudden increase in pop-up ads or error messages, particularly those asking for personal information, can signal the presence of a Trojan.
- Strange Network Activity: If your computer is sending or receiving data without your knowledge, this could indicate that Wacatac is transmitting stolen data to a remote server.
- Unexplained System Crashes: Trojan infections can cause instability, leading to unexpected crashes or restarts.
How to Scan for Trojan: Win32/Wacatac?
To check if your system is infected with Wacatac, use a reputable antivirus or anti-malware software to perform a deep scan of your computer. These programs are designed to detect Trojans and other types of malware that may be hidden in your system.
Reminder: Always keep your antivirus software up-to-date to catch the latest threats, as malware signatures are constantly evolving.
What Are the Dangers of Trojan: Win32/Wacatac?
While the stealthy nature of Wacatac makes it difficult to detect, the dangers it poses are far-reaching. Once installed, this Trojan can lead to serious consequences, including:
Data Theft and Privacy Breach
One of the most significant risks of Trojan: Win32/Wacatac is its ability to steal sensitive information. This can include login credentials, banking details, and personal identification data. Cybercriminals use this stolen data for identity theft or to access accounts, which can result in financial losses and personal harm.
System Instability and File Corruption
Wacatac can damage or corrupt system files, leading to performance issues, crashes, or complete system failure. If left unchecked, this Trojan could render your computer unusable and lead to data loss.
Remote Control and Botnet Formation
In some cases, Wacatac can allow cybercriminals to gain remote access to your system. This opens the door for them to control your device, install additional malware, or even turn your computer into a bot in a botnet attack. This can be used to launch attacks on other systems or perform other malicious activities.
How to Remove Trojan: Win32/Wacatac?
If you suspect that your system is infected with Wacatac, it is essential to act quickly. Here’s what you can do to remove the infection:
- Use Antivirus Software: Run a full system scan using a reputable antivirus tool to detect and remove Wacatac.
- Delete Suspicious Files: Manually check your system for any suspicious files or programs that may be associated with the Trojan and delete them.
- Update System Software: Ensure that your operating system and software are up-to-date to fix any vulnerabilities that could be exploited by malware.
- Seek Professional Help: If the Trojan persists or has caused significant damage, it may be best to consult a professional IT technician for further assistance.
Note: Always backup your important data regularly to avoid losing it in case of malware infection.
Steps to Protect Your System
| Protection Method | Description |
| Install Antivirus Software | Use reliable antivirus software to detect and block threats. |
| Enable Firewall Protection | Set up a firewall to block unauthorized access to your system. |
| Avoid Suspicious Downloads | Do not download files or open email attachments from unknown sources. |
| Keep Software Updated | Regularly update your operating system and programs to fix security vulnerabilities. |
Conclusion
Trojan: Win32/Wacatac is a serious and stealthy threat to your computer and personal data. Because it operates silently, it is often difficult to detect, but the consequences of an infection can be severe. From data theft to system corruption and remote control, the dangers posed by this Trojan are not to be underestimated.
Protecting yourself from Wacatac involves maintaining good cybersecurity practices, such as using antivirus software, avoiding suspicious downloads, and keeping your system up to date. If you suspect your computer has been infected, act quickly to run a system scan and remove the Trojan as soon as possible to minimize the damage.
By staying vigilant and taking preventive measures, you can safeguard your system from this hidden threat and other cyber risks.
FAQ’s
- What is Trojan: Win32/Wacatac?
Trojan: Win32/Wacatac is a Trojan horse malware that infiltrates Windows systems, steals data, and can remotely control the infected computer. - How does Trojan: Win32/Wacatac spread?
This Trojan spreads through malicious email attachments, unsafe downloads, or phishing attacks that trick users into running infected files. - What are the signs of Trojan: Win32/Wacatac infection?
Symptoms include slow system performance, unexpected pop-ups, unexplained crashes, and strange network activity. - How do I remove Trojan: Win32/Wacatac from my computer?
Use antivirus software to scan and remove the Trojan, delete suspicious files, and update your system to secure it against future attacks. - How can I protect my computer from Trojan: Win32/Wacatac?
Use antivirus software, enable firewalls, avoid suspicious downloads, and keep your system and software updated regularly to reduce the risk of infection.